Data in Synology NAS are Encrypted by SynoLocker? SynoLockeR Ransomware Demands Bitcoins
Recently, many computers may have heard about a group ramsomware called SynoLocker has attacked a network-attached storage devices made by Synology. Some users’ data on Synology NAS has been hacked b y this newly ransowmare and most of the data are encrypted.
File-encrypting malware known as SynoLocker mainly targets Synology NAS Devices, and as soon as it gets installed, this malware locks the user out of the control panel and proceeds to encrypt all files stored on the NAS. Similar with the CryptoLocker ransomware where it will basically lock up a computer while encrypting files then ask for a payment for decrypting those files. If users want to decrypt the files, a ransom of 0.6 Bitcoins - around £210 (approximately $350 USD) - is demanded. Users need to pay anonymously via for the decryption key. SynoLocker exploits vulnerabilities in older versions of Synology's Diskstation Manager (DSM) operating system
Full SynoLocker ransom message, courtesy the Synology German User forum (via CSO)
“SynoLocker™
Automated Decryption Service
All important files on this NAS have been encrypted using strong cryptography.
List of encrypted files available here.
Follow these simple steps if files recovery is needed:
Download and install Tor Browser. Open Tor Browser and visit http://cypherxffttr7hho.onion. This link works only with the Tor Browser.
Login with your identification code to get further instructions on how to get a decryption key.
Your identification code is - (also visible here).
Follow the instructions on the decryption page once a valid decryption key has been acquired.
Technical details about the encryption process:
A unique RSA-2048 keypair is generated on a remote server and linked to this system.
The RSA-2048 public key is sent to this system while the private key stays in the remote server database.
A random 256-bit key is generated on this system when a new file needs to be encrypted.
This 256-bit key is then used to encrypt the file with AES-256 CBC symmetric cipher.
The 256-bit key is then encrypted with the RSA-2048 public key.
The resulting encrypted 256-bit key is then stored in the encrypted file and purged from system memory.
The original unencrypted file is then overwrited with random bits before being deleted from the hard drive.
The encrypted file is renamed to the original filename.
To decrypt the file, the software needs the RSA-2048 private key attributed to this system from the remote server.
Once a valid decryption key is provided, the software search each files for a specific string stored in all encrypted files.
When the string is found, the software extracts and decrypts the unique 256-bit AES key needed to restore that file.
Note: Without the decryption key, all encrypted files will be lost forever.
Copyright © 2014 SynoLocker™ All Rights Reserved.”

How to Complete the Decryption Process Caused by SynoLocker
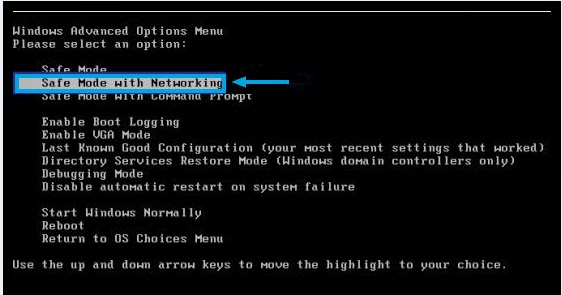
Step One: Restart your PC into Safe Mode with Networking.
*For Windows 7/Vista/XP users:
a. Restart the computer. Before Windows Welcome interface appears, please tap F8key constantly until Windows Advanced Options Menu displays.
b. On the black screen of Windows Advanced Options Menu, use the arrow key to move down and choose Safe Mode with Networking option by highlighting it. Then hit Enter on the Keyboard.
*For Windows 8 users:
a. Select Settings on the charm bar and then Power options. Press and hold Shift key on the keyboard and click Restart.
b. Click Troubleshoot on the displaying Choose an option menu and then Advanced option to proceed.
c. Choose Windows Startup Settings next and press Restart. After that, the computer will reboot and show nine start-up settings, click F5 to enter.
Step Two: Run a computer scan with SpyHunter Anti-Malware to remove SynoLocker
SpyHunter is a powerful Anti-Malware to detect and remove all traces of malware including worms, Trojans, rootkits, rogues, dialers, spyware and more.
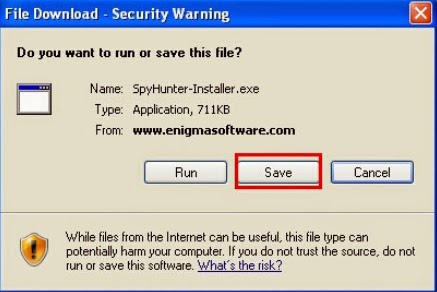
1: Download the latest official version of SpyHunter by click the below download icon.
2: Once you have downloaded, double-click the installer file to start the installation.

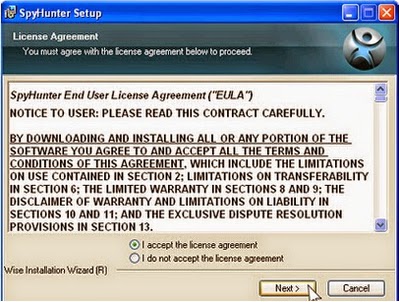
3: Keep following the prompts shown on the screen in order to continue with the installation process.


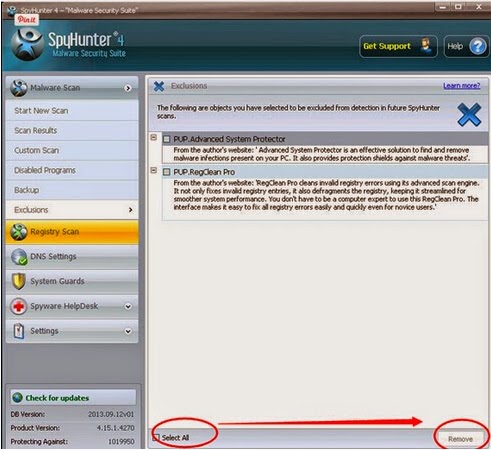
4: When installing done, please start a full scan with your system.

5: After the scanning, please check the results and remove all infected files.
Step Three: Restart your PC back to normal mode.
Announcement: To protect your data being encrypting by SynoLocker, please be careful on surfing internet. If you have hacked by this malware, you have to remove it by using removal tool. Please don’t pay fine to SynoLocker.
No comments:
Post a Comment